What is Firewalld and It’s Predefined Zones
Firewalld is a powerful and simple to use tool to manage a firewall on CentOS/RHEL 8 Server. By default, few services to receive incoming traffic are enabled. You can set up rules to either block or allow traffic. In CentOS/RHEL 8 nftables replaces iptables as the default Linux network packet filtering framework.

Useful Articles:
- LINUX FIREWALL – BASIC GUIDE OF IPTABLES
- HOW TO SET UP A FIREWALL USING FIREWALLD ON CENTOS/RHEL 8
- BLOCK COUNTRIES USING CSF FIREWALL ON LINUX
- USE OF CSF FIREWALL IN LINUX
- INSTALL CSF (CONFIGSERVER FIREWALL) ON LINUX
- HOW TO INSTALL PROFTPD SERVER ON RHEL/CENTOS 7
Basic Concepts in Firewalld
Basically, there are two main concepts that need to understand on Firewalld.
Zones
Each zone can be configured to allow or deny services/ports. The zone can be associated with one or more network interfaces.
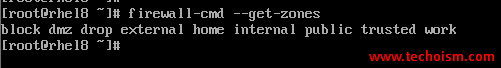
# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
Understanding Predefined Zones
drop: All incoming connections are dropped only outgoing connections are possible.
block: Similar to the drop zone, It’s dropping all the connections only connections within the system are possible.
public: You don’t trust other computers but may allow selected incoming connections and allow required ports and services.
dmz: Demilitarized zone (DMZ) provides limited access to your LAN and only allows selected incoming ports.
external: You need LAN and WAN interfaces too for masquerading (NAT) to work correctly. Useful for router type of connections.
home: Useful for home computers such as laptops and desktops within your LAN where you trust other computers. Allows only selected TCP/IP ports.
internal: For use on internal networks when you mostly trust the other servers or computers on the LAN.
trusted: All network connections are accepted. We do not recommend this zone for dedicated servers or VMs connected to WAN.
work: For use at your workplace where you trust your coworkers and other servers.
Services
A service is nothing just a list of local ports, protocols, source ports, destinations, and firewall helper modules.
Port – 443 or 80 or 3306 Service – SSH, HTTP, FTP
Reference: https://firewalld.org/
Enjoy it!
