How to Install and Use Linux Malware Detect (LMD)
Linux Malware Detect (LMD) is a malware scanner for Linux distribution, Which is released under the GNU GPLv2 license. That is especially designed to find the threats in shared hosted environments because in shared environment thousand plus users are sharing the resources. Each and every user will upload different things and script, etc., It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection.

LMD Features
Download Linux Malware Detect
Linux Malware Detect is not available in any online repository. So you need to download the source code of LMD using below command:
# wget http://www.rfxn.com/downloads/maldetect-current.tar.gz
Extract and Install Linux Malware Detect
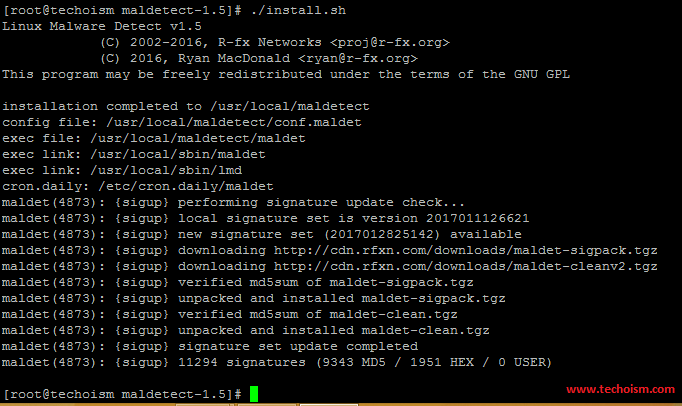
After downloading the source code you need to extract the archive file and install the Linux Malware Detect following below steps.
# tar -xvf maldetect-current.tar.gz # cd maldetect-1.5 # ./install.sh
Configure Linux Malware Detect
You need to configure LMD through “/usr/local/maldetect/conf.maldet” configuration file. By default all the option are commented in configuration file so we need to do changes accordingly.
# vim /usr/local/maldetect/conf.maldet
# To get email alert # email_alert=1 # Add your e-mail id to get email alert # email_addr="anuketjain.2099@yahoo.in" # Add email subject # email_subj="Malware alerts for $HOSTNAME - $(date +%Y-%m-%d)" # To move malware to quarantine & alert # quarantine_hits=1 # Clean injected malware # quarantine_clean=1 # To suspend/disable your wish # quarantine_suspend_user=0 # To set minimum user id that can be suspended # quarantine_suspend_user_minuid=500
Note: You can do changes as per your requirement.
Scan the System
After configuring, you can scan the system manually using the following command:
# maldet --scan-all /
Linux Malware Detect v1.5
(C) 2002-2016, R-fx Networks
(C) 2016, Ryan MacDonald
This program may be freely redistributed under the terms of the GNU GPL v2
maldet(8097): {scan} signatures loaded: 11294 (9343 MD5 / 1951 HEX / 0 USER)
maldet(8097): {scan} building file list for "/", this might take awhile...
maldet(8097): {scan} setting nice scheduler priorities for all operations: cpunice 19 , ionice 6
maldet(8097): {scan} file list completed in 0s, found 20620 files...
maldet(8097): {scan} scan of "/" (20620 files) in progress...
maldet(8097): {scan} scan completed on "/": files 20620, malware hits 0, cleaned hits 0, time 117s
maldet(8097): {scan} scan report saved, to view run: maldet --report 170210-0351.8097
After scanning, you can examine malware scan report by running the following command:
# maldet --report 170210-0351.8097
HOST: techoism.com SCAN ID: 170210-0351.8097 STARTED: Feb 10 2017 03:51:48 -0600 COMPLETED: Feb 10 2017 03:53:45 -0600 ELAPSED: 117s [find: 0s] PATH: "/" TOTAL FILES: 20620 TOTAL HITS: 0 TOTAL CLEANED: 0 =============================================== Linux Malware Detect v1.5 < proj@rfxn.com >
You can also scan the specific filesystem on server.
# maldet -m /var,/home,/opt
Quarantine the Infected Files
Run the following command with the scan report ID to clean the effected files.
# maldet -q 170210-0351.8097
Update LMD & Signatures to Latest
Use below both command to update your LMD version & virus signatures to latest.
# Update the installed version #
# maldet -d
# Update malware detection signatures #
# maldet -u
Enjoy it!