Why is Linux more secure than windows and any other OS?
Linux is an open operating system, the codes which can be read by everybody, yet at the same time acknowledge more secure in correlation with different OS. Have you ever known about any Linux System being influenced by Virus? Most servers run Linux for the reason in light of the fact that it is so secure. The filesystem that Linux uses gives many features that Linux security infrastructure uses, file/directory ownership and privileges being a very important one of them.

Before we proceed onward to specialized issues, I will advise you that one hundred percent shielded from hackers operating system does not exist. That is the reason, whether you picked Linux or Windows, the essential point is to install applications to ensure security in the selected system. Here I will try to throw some of the security highlights which I know in Linux and trust that these points secure the Linux Operating System.
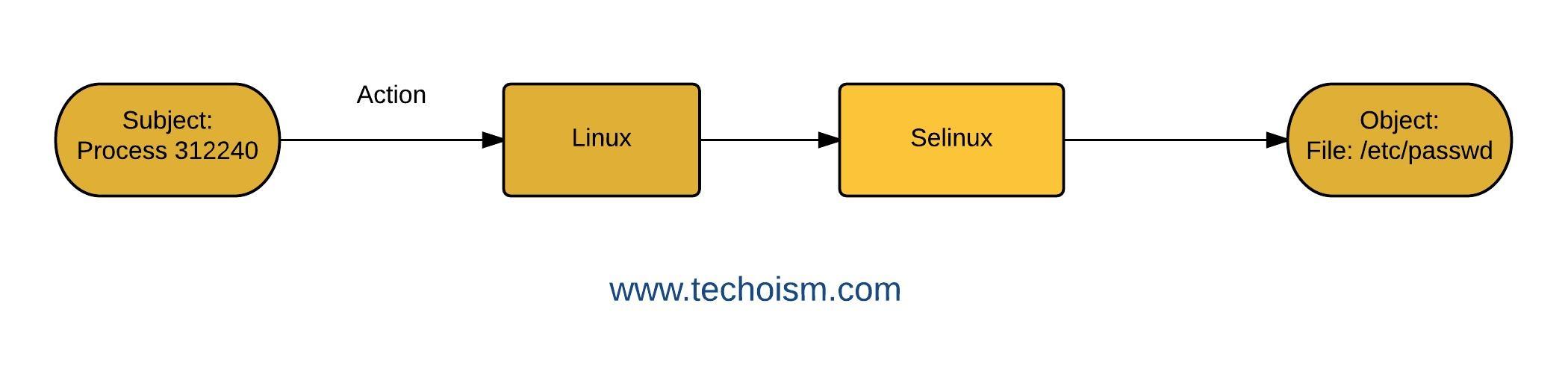
1# SElinux (Security Enhanced Linux)
Security-Enhanced Linux (SELinux) is a Linux features that gives the component to supporting access control security policies. Selinux implements the thought that programs ought to be constrained in what files they can access to and what actions they can make. SELinux is a kernel security extension, which can be used to prepare for misconfigured or comromised programs. It comes with Mandatory Access Control (MAC) system that enhances the traditional UNIX/Linux DAC (Discretionary Access Control) model.
SELinux defines the access and transition privileges of each user, application, process, and file on the system. On a day-to-day basis, system users will be largely unaware of SELinux. Just system administrators need to consider how strict a policy to implement for their server environment.
For more information please follow the below link.
Introduction of Selinux in CentOS/RHEL
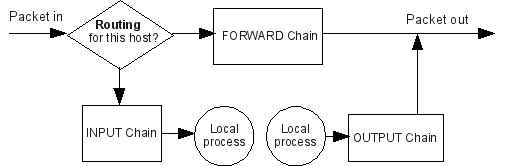
2# IPtables
IPtables is a simple firewall installed on most linux distributions and with the IPtables you can implement a greater level of security for your Linux machine.. Firewall decides fate of packets incoming and outgoing in system. IPtables is a rule based firewall and it is pre-installed on most of Linux operating system. By default it runs without any rules.
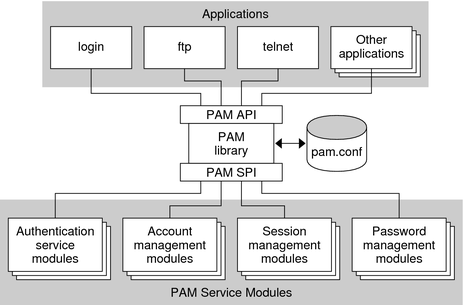
3# PAM (Pluggable Authentication Modules)
Linux-PAM is a system of libraries that handle the authentication tasks of applications (services) on the system. Linux-PAM separates the tasks of authentication into four independent management groups: account management; authentication management; password management; and session management.
Authentication: This module interface authenticates use. For example, it requests and verifies the validity of a password. Modules with this interface can also set credentials, such as group memberships or Kerberos tickets.
Account: Account provides verification types of service. For example, it may check if a user account has expired or if a user is allowed to log in at a particular time of day.
Session: This module interface configures and manages user sessions. Modules with this interface can likewise perform additional tasks that are expected to permit access, such as mounting a user’s home directory and making the user’s mailbox box available.
Password: This module interface is used for changing user passwords.
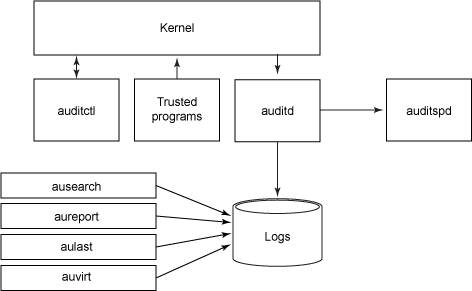
4# Audit
auditd is the user-space component of the Linux auditing subsystem. It’s responsible for writing audit records to the disk. When auditd is running audit message sent by the kernel will be collected in the log file configured for auditd (normally /var/log/audit.log). If auditd is not running for any reason kernel audit messages will be sent to rsyslog.
Enjoy it!

sdsfdg